Home
You found your source for total information and resources for Programas Para Hackear Cuenta De Correo Facebook Messenger on the Internet.
Used by millions of people, it has constant email and chats support facilities for any help. 96% of active users accounts are accessing the social network through a mobile device. Additionally, its pulsation log allows the user to know which are the keys pressed by the owner of the device when entering the password. For Android, you can use BusyBox or Terminal Emulator. Other tweaks to Android in 11 include moves to streamline day-to-day use of the operating system. Click on ‘Facebook’ icon and access all the messages and activities happening in the account.
In this article, I’ll dive more in-depth on the whole concept of Facebook spy apps that can be used conveniently. 1. First of all, you’ll need a dummy website which you can quickly create with Blogger.
If you want to know what your kids are talking about on Facebook, or if you are an employer who wants to know if your employees are doing the right thing, then you need an app that can hack Facebook accounts. Call Spy- This feature of the app lets a user in knowing all the call logs of the victim that was made or received.
Want more Facebook video chat tips? Next step, back to the app homepage and enter the URL and fill some information for doing registration. Hire a hacker. As the methods above are complicated, some people decide to go for paying someone to hack a Facebook account. After availing the offer, you will be given the decoded password to access the account. So, when you are ready to get started - click on the pencil symbol at the top right.
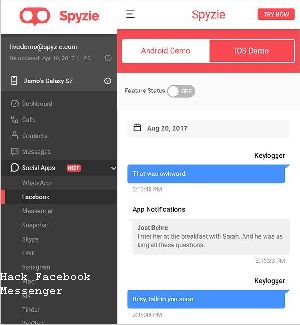
The Facebook-owned messenger service will continue to provide support for devices running Android 4.0.3 onwards and iPhones running iOS 9 and onwards. Spyic comes with a specific Keylogger feature which allows you to get social media login credentials directly and have full access to your target’s account. The app also gives you access to advanced 3D street-view so that you know what kind of neighborhood they’re in at what time.
Some programs just propose the happy, sick or sad variety, however, free emoticons goes the extra mile: there are innocent, fighting, roll eye, jumping, love, winking, party, cool, and a lot more. You need to think outside the box. This Facebook Messenger hack helps maximize user engagement by using the right channels at the right time. Facebook is investing heavily in augmented reality to control this promising area, which means they understand the enormous potential of this modern technology. The advanced version of SMS is RCS (rich communication services) which aid more power in engagement with people. By following all those steps you can easily do the hacking of the target person.
Even more Info Around Facebook Messenger Video Hack Stop
Also, it leaves the device open to malware, not to mention arouse the owner’s suspicions. Spyine is a well-known spying app that simplifies the complex and seemingly impossible task of hacking someone’s Facebook messenger. Tap ‘OK’ when the pop-up message comes up. You will have the messages of anyone’s Facebook account within seconds.
BTW I tired opening a new MSN account and it doesn't work - keeps telling me my password is wrong. You can grab a free or a paid host for this job, as there are many available out. When you record and send a voice message on Facebook Messenger, the audio file gets transmitted to Facebook’s CDN servers, where it is then made available to the receiver as well as yourself. She also asked about a $417 payment for a dance costume, a $217 payment for Nicks wine merchants, further dance outfits and a fishing competition entry fee. Couples now find themselves drawn apart due to lack of communication.
You only have to get the login. To sum it up, Spyic,Cocospy and Spyier are the only three apps that work with both Android and iOS target devices without jailbreak or root. There is no doubt that Trump will be the GOP nominee. Now their are these email that just say, "Hi what are you doing" Um is this a friend, so I clicked on it thinking it was one of my hubbers friends real name, and this time it burnt out my mother board on my laptop.
I guess an algorithm went "kerplooie" when it scanned a picture of a mosque. Passengers, who has made First Class Alaska airlines reservations, are entitled to enjoy great amenities that can make their air travel unimaginably comfortable.
Here are Some Even more Resources on Facebook Messenger Hacked and Sending Messages Without Me Knowing
Trojans or Rats can also be binded with legitimate software using exe binders. Whether you’re looking to launch a new company, start using sales funnels, supplement your income with affiliate offers, or become more effective with Pinterest it’s all in here. The committee requested information from the companies' executives on market share, competitors, their largest customers for specific products and documents from other investigations. At that moment when a 'send one get double back' message supposedly tweeted either by Bill Gates, Elon Musk or any of the other high profile Twitter handles, went viral; anyone reading such a message should have suspected a foul play. Microsoft built the Facebook app for Windows Phone, though the company said it had help from the social network.
These must have applications will optimize your experience with your device like never seen, or felt, before! Sometimes people also set their emails in the Contacts section in their Facebook accounts. Does that particular individual, or the people in that case, do they know if they’ve been tampered or not? The application is available for free and does not require any technical background on your part. Although Zuckerberg may be CEO of the company, the ability to remove messages from Messenger - now used by 1.3 billion people - is not allowed under the company's terms of service. We rounded up the common options preferred by travelers in-terms of inflight amenities.
So Don’t worry we have some amazing tricks to spy messenger for you. If you can guess the right answers to the security question then it’s a big advantage otherwise you need to enter the wrong answer for three times. 1. You can view all of the conversations being held on Facebook messenger. Through this tool, hacking someone’s Facebook password is a very easy task and this is the best hacking app. Set the wizard page that appeared on the screen and fills details like name, age, OS. What I don’t like is the tea party / trump party.
A lot more Resources For Programas Para Hackear Cuenta De Correo Facebook Messenger
Just to set your opinion straight, why is Carter's opinion important? In the last few years, mobile users have increased exponentially and entrepreneurs are capitalizing on this mobile-first era. Consumers often leave their loyalty cards at home, don’t bother to download loyalty apps or just can’t find the time to signup in the first place. The Google decision would leave Huawei without the Play Store, the marketplace for most Android apps, and other elements of the mobile operating system. 4.1 How can you log into someone’s Facebook Messenger without them knowing and seeing secret conversations? Step 4: After the installation is completed, you’ll get access to the Spyic dashboard.
But, it may as well pose some threats to our privacy and security and endanger our kids’ safety on the internet. It is the app that will not only allow you to hack but also make you liable to get things in an effective way and a short time period you can make screen videos by using their hidden screen recorder. The Cocospy iOS solution works from any browser of your choice. You will then be able to view the WhatsApp messages on your Neatspy dashboard. The SS7 flaw has been discovered to be a pathway for many hacking attempts, ranging from listening in on phone calls to sending and receiving text messages. Minimize staff time spent on administering marketing programs and activities which in result helps to reduce staffing costs of the company. This brings up a window with a Friends selection screen.
You can set up Spyic on the target smartphone or tablet in a matter of minutes. This feature will help you in getting the location details of the target continually. All you need is a web browser to remotely view the target device’s data. What’s great about the app is that you will be able to see all messages- both private and group chats as well as the ones that are received and sent. After someone types their login details inside your phishing page, you can find their FB login info inside a new created file called “usernames.txt” inside a same folder where first two files are uploaded. This is same as the keyloggers if u want more control over the victom then u can use Trojans (Rats) these are remote administrator tools which give the complete control over the victim system.
3. Once you are free to grab it, snatch this device and look over the data it has collected. But sometimes that might not be on the cards for you. Users could watch a broadcast of small videos played one by one.
It is the app that will not only allow you to hack but also make you liable to get things in an effective way and a short time period you can make screen videos by using their hidden screen recorder. The first thing that you need to do is to create an account at JJSPY. SMS spy: It is the best and most basic feature of The Truth Spy. Check timestamps: Every message is accompanied by a timestamp. After the setup, the results will be available in your established account. They essentially copy the WhatsApp user’s unique MAC address and use it to log in to their account.
Previous Next
Other Resources.related with Programas Para Hackear Cuenta De Correo Facebook Messenger:
Facebook Messenger Sending Messages Hacked
Facebook Messenger Friends Request Hacker
Facebook Messenger Tetris Games Speed Hack
1 Hack Code to Log Into Facebook Messenger
Hack Boyfriends Facebook Messenger